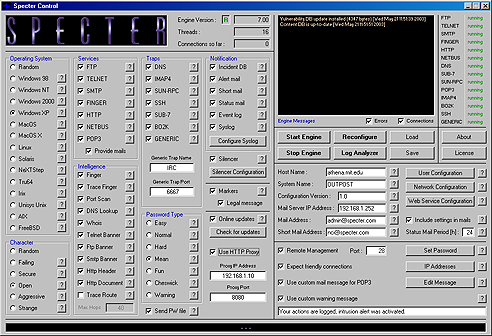
Configuration
SPECTER comes with a GUI called Specter Control. It is used for configuration as well as for checking the current state of the honeypot. SPECTER can also be configured remotely from any workstation running Windows 98/ME/NT/2000/XP.
The Specter
Control main
window:
Click on image to open full version in separate window
Incident
Management
SPECTER comes with a powerful tool called the Log Analyzer. It can search through the incident database and display all logged information about a specific incident in a clearly arranged window. Various filters can be combined to search for specific incidents.
Click on image to open full version in separate window
Click on image to open full version in separate window
Simulated operating system
SPECTER simulates 14 different operating systems:
Windows 98
Windows NT
Windows 2000
Windows XP
Linux
Solaris
Tru64 (former Digital Unix)
NeXTStep
Irix
Unisys Unix
AIX
MacOS
MacOS X
FreeBSD
Note: SPECTER Light only simulates Windows NT, Windows 2000 and Windows XP
There are 5
different characters available for the simulated host:
Open - The system behaves like a badly configured system in terms of security.
Secure - The system behaves like a well configured system in terms of security.
Failing - The system behaves like a machine with various hard- and software problems.
Strange - The system behaves unpredictable and leaves the intruder wondering what's going on.
Aggressive - The system communicates as long as necessary to collect information about the attacker, then reveals its true identity by the appropriate means depending on the kind of connection and then ends communication. This is very handy to scare intruders away.
If the system character is set to "Open", "Strange" or "Failing", the simulated machine appears to be suffering from various vulnerabilities depending on the selected operating system and services/traps. The vulnerabilities change randomly to make it virtually impossible to detect a SPECTER system based on the combination of its vulnerabilities.
SPECTER offers 14 different network services and traps. All connections are logged with the IP address of the remote host, exact time, type of service and state of the honeypot machine at the time of the connection. Depending on the type of service/trap and the intelligence settings, there is much more information logged, such as a complete protocol log, content of mails sent etc. The available services and traps are:
SMTP
FTP
TELNET
FINGER
POP3
IMAP4
HTTP
SSH
DNS
SUN-RPC
NETBUS
SUB-7
BO2K
GENERIC TRAP
Notification
SPECTER can log to its own incident database, to the system's event log or to a remote Syslog server. It can send alert mail messages right when something is happening. It can also send short alert mails suitable for redirection to mobile phones and pagers. Additionally, SPECTER can send status reports on a regular basis.
Intelligence
SPECTER offers various intelligence modules to collect information about attackers as well as evidence against them. The available intelligence options are:
FINGER
TRACER
PORTSCAN
TRACEROUTE
TELNET BANNER
FTP BANNER
SMTP BANNER
HTTP SERVER
HEADER
HTTP DOCUMENT
WHOIS
DNS
Markers! (pat.
pending)
SPECTER dynamically
generates more than 100 different executable programs for
various operating systems that will leave up to 32 hidden marks on an attacker's
computer. The information contained in the marks can be valuable evidence in
court.
If you are an officer of a law enforcement agency and need to locate SPECTER marks on a confiscated computer,
contact markers@specter.com. Please note that proper authentication will be
required.
Custom user names and logins
SPECTER comes with hundreds of default user names and logins well-suited for english-speaking environments. To further improve the integration of the SPECTER system into your network, or if the common language in your organization is not English, custom user names and logins can be entered. Use the names and logins of real people working for your organization to make the honeypot perfect. Custom and default user names can be mixed.
Custom content
SPECTER comes with massive amounts of decoy data, but you can add your own content to make the honeypot look even more like one of your production machines. For example, you can provide your own web documents for the simulated HTTP server.
Fake password files
SPECTER can provide fake password files to intruders. It can send password files in 3 different formats:
Unix passwd
NT/W2K/XP binary uncompressed
NT/W2K/XP binary compressed
What kind of file is provided depends on the simulated operating system and the way an attacker tries to get the password file.
The type of the password files can be specified. There are 7 types available:
Easy - Easy to guess
passwords.
Normal - Normal
passwords, some weaker, some stronger.
Hard - Hard to guess
passwords.
Mean - Very strong,
extremely hard to guess passwords.
Fun - Famous
people as user names and appropriate passwords.
Cheswick - The famous
password file from the well-known book "Firewalls and Internet
security" by William R. Cheswick and Steven M. Bellovin.
Warning - The file sent is not a password file but a text file containing a configurable warning message.
DOS attack and
flooding countermeasures
While a honeypot typically doesn't experience heavy traffic, it can still become the target of DOS, DDOS or flooding attacks. SPECTER features various mechanisms to handle such attacks. Most of them work automatically, others can be enabled/disabled and configured, such as the connection throttle and the flood blocker. The silencer module prevents notification flooding.
Online updates
The vulnerability and the decoy content databases can be updated automatically once a week. This allows the honeypot to change constantly without user interaction.
Help
SPECTER comes with full-featured, searchable online documentation. Additionally, there is a feature called Specter Instant Help. For almost every element, there is a small built-in help window just a click on the corresponding Instant Help-button away.
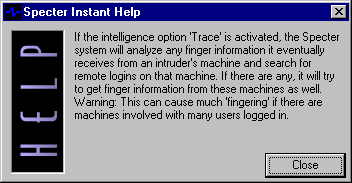
Instant Help Example
Conclusion
The operating system and character options combined with the services, traps, password and other settings allow SPECTER to act and appear in more than 950 million different ways. The use of custom user names, web pages, mail messages, logins and other customization options further increases that number to billions. Randomly changing vulnerabilities add another layer of obfuscation. Therefore, it is virtually impossible for an attacker to detect a SPECTER system by looking for certain configurations, vulnerabilities or combinations of network services.
The variety of available operating systems
and configuration options allows SPECTER to be
integrated perfectly into any
environment. Because of the easy to use GUI tools, any system administrator
with basic
networking knowledge can set up a professional honeypot in less than half an
hour. SPECTER produces detailed protocol logs for technical analysis, but by
adding clear text comments to these logs about what exactly is going on, SPECTER makes
it possible for everybody to read the logs and draw useful
conclusions without knowing every low-level detail about a
certain protocol by heart.