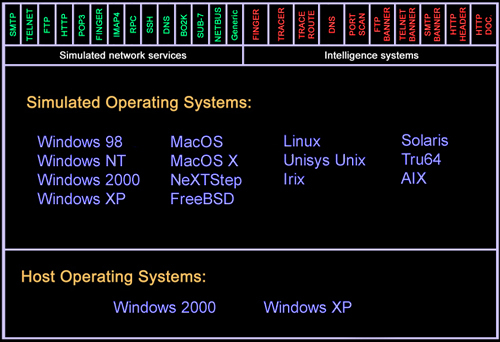
What is SPECTER?
SPECTER is a smart honeypot or deception system. It simulates a complete machine, providing an interesting target to lure hackers away from the production machines. SPECTER offers common Internet services such as SMTP, FTP, POP3, HTTP and TELNET which appear perfectly normal to the attackers, but in fact are traps for them to mess around and leave traces without even knowing that they are connected to a decoy system, which does none of the things it appears to do but instead logs everything and notifies the appropriate people. Furthermore, SPECTER automatically investigates the attackers while they are still trying to break in. SPECTER provides massive amounts of decoy data, and it generates decoy programs that will leave hidden marks on the attacker's computer. Automated weekly online updates of the honeypot's content and vulnerability databases allow the honeypot to change constantly without user interaction.

How does it work?
A SPECTER system consists of a dedicated PC and the SPECTER software. It gets connected to the network where attacks are expected to occur. This usually means to place it as close to the Internet as possible, typically in the DMZ. But SPECTER can also be installed on internal networks to find out about suspicious activities originating from within an organization.
Another interesting possibility is to install SPECTER on a production machine such as a mail server. In this scenario, the SMTP service is real while all other network services on the machine are simulated by SPECTER. If an attacker connects to the machine looking for vulnerabilities, he will very likely connect to one of the simulated services and find what he is looking for. But while he thinks he's breaking in, he has actually triggered an alert, he's investigated, everything he does is logged and at the same time the mail server is absolutely safe.
What are the main advantages?